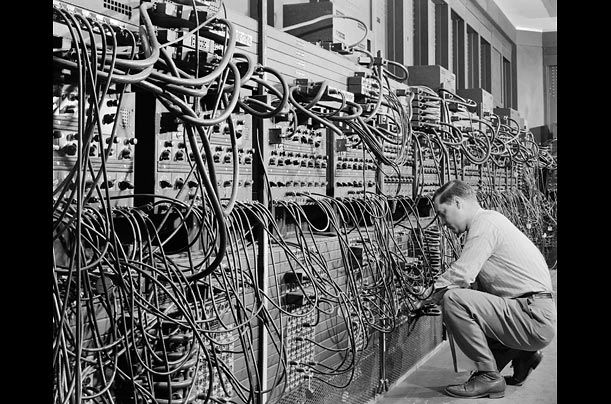
Generation of Computer
Each generation of computer is characterized by a major technological development that fundamentally changed the way computers operate, resulting in increasingly smaller, cheaper, more powerful and more efficient and reliable devices.
The iPad is one of the hottest gadgets of 2010
The iPad essentially revolutionises the concept of a tablet computer. Previously tablet devices addressed a legitimate consumer need (casual, lazy, couch-bound computing), but left most people frustrated with a stylus-driven handwriting recognition system and an operating system that was really designed to be used on a desktop PC.
The Technology of Mobile Phone
Mobile phones also support a wide variety of other services such as text messaging, MMS, email, Internet access, short-range wireless communications (infrared, Bluetooth), business applications, gaming and photography. Mobile phones that offer these more general computing capabilities are referred to as smartphones.
The Technology of Internet
The Internet is a global system of interconnected computer networks that use the standard Internet Protocol Suite (TCP/IP) to serve billions of users worldwide.
The Categories of Software
Software is often divided into application software (programs that do work users are directly interested in) and system software.
Ethics in Computer

** from Module from BPK - Ethics in Computer
Installing and Uninstalling Application Software
Steps you should take before you Install Software.
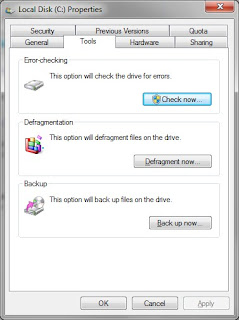 Click the Check Now button-check the Automatically fix system errors-click Start. It will tell you it cannot run now and will run at the next boot, click Ok and restart the computer.
Click the Check Now button-check the Automatically fix system errors-click Start. It will tell you it cannot run now and will run at the next boot, click Ok and restart the computer.
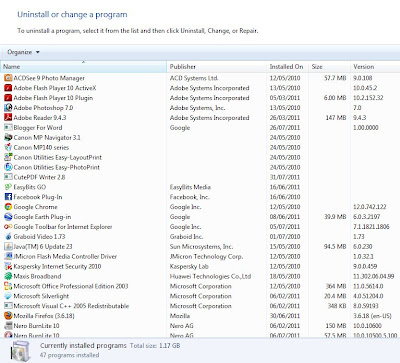
2) Uninstalling Software
Cyber Law
What is Cyber Law?
Cyber law refers to any laws relating to protecting the Internet and other online communication technologies.
NEEDS FOR CYBER LAW
- In the recent years, many concerns and issues were raised on the integrity and security of information, legal status of online transactions, privacy and confidentiality of information, intellectual property rights and security of government data placed on the Internet.
- These concerns and issues clearly indicate why cyber laws are needed in online activities.
- The need for cyber law :
1) Integrity and Security of Information
2) Security of Government Data
3) Legal Status of Online Transactions
4) Intelectual Property Rights
5) Privacy and Confidentially of Information
THE CYBER LAW ACTS IN MALAYSIA
- The Malaysian Government has already passed several cyber laws to control and reduce the Internet abuse.
These cyber laws include:
- Digital Signature Act 1997
- Computer Crimes Act 1997
- Telemedicine Act 1997
- Communications and Multimedia Act 1998
Beside these cyber laws, there are three other cyber laws being drafted.
- Private Data Protection Bill
- Electronic Government Activities Bill
- Electronic Transactions Bill